***
The programmer's son comes up to his father and asks:
- Dad, what is PENGUIN?
Dad (thoughtfully):
– Ping… Win... Ping Windows, then. Function for detecting Windows hangs ...
Probably everyone noticed that when connecting to the Internet via dial-up-modem connection speed gradually drops. The fact is that when new users connect to the provider's server, the connection speed decreases (especially if the provider's server "seems" that your modem is not active).
All this allows you to immediately see the entire network, get fast access to network management and simplify network navigation. A wizard will help you find all the devices on your network and use this information to create a network card. Several procedures are provided. With various search methods, you can find almost all devices and get information about them.
What is ping?
You can add devices, links between them, arrows, lines, text blocks, hyperlinks, images, links to other maps to the map. You can resize them, format them, change the style. This allows you to create network cards with an unlimited number of devices with a starter license! The app includes a wide range of network devices. All devices are grouped into categories, Computers, Peripherals, Network, Satellite, Rack, Shop Equipment, Links, Construction.
To restore the connection speed, you can use the so-called ping.
What is pinging
– ping (english... abbreviation from Packet InterNet Groper - packet sender Internet) Is a program used to check the availability of the addressee on the network by sending him a special signal ( ICMP echo request - request response ICMP) and waiting for a response.
It is planned to import new collections of equipment and create new types of devices. This allows you to create a complete and accurate network map. Vector graphics are used to draw the map. This improves the quality of map scaling and device resizing. Raster graphics also supported.
Advanced navigation tools
Various tools can be used to create map topology and make navigating large maps easier.
Description of network devices
In the description of power supplies, you can add additional fields, Add image, contact information, location, owner. You can create your own fields. Hyperlinks and addresses email are automatically detected. For your convenience, additional fields are grouped. You will immediately have access to the information you need.– pinging - test polling of a remote object.
– ICMP (English abbreviation for Internet Control Message Protocol - protocol of control messages in the network Internet) Is one of the four inter-network layer protocols of the family TCP / IPthat ensures communication recovery in case of failure situations in the transmission of user packets.
By the way, a simple (not abbreviated) word ping (english.) means whistling; hum; ringing; whistle; to hum... Maybe that's why the modem whistles, buzzes and rings when connected? Joke!..
Automatic channel creation
The status of network devices is displayed on the map. Detailed information is displayed when the device is traversed with the mouse. Connections between devices are drawn as lines on a map. They are created in a few clicks. Lines are created automatically and evenly between devices. Likewise, you can link additional devices and the old lines will automatically move so that the new ones can fit evenly. This avoids time-consuming hand-drawing and concentrates on basic tasks.
For pinging, you can use the standard utility of the operating system. But first you need to find out server.
How to find out the servers
a) Windows Vista:
- connect to The Internet;
- press Start -\u003e Connect;
- in the opened window Connect to the network click right click mouse connection required;
The network speed is also displayed. This could be due to connectivity issues, routing issues, or simply a firewall between the server and the monitoring station. Our commercial licenses with many sensors can be found here.
With an intuitive web interface, you can manage the system, customize reports, and share results with your colleagues and clients in real time. The answer is through the subsystem of the operating system, which is responsible for exchanging information. No applications should start, they don't need access to any files, they don't need to be configured and practically not affect other actions. Ensure that all hardware, gateways, routers, firewalls, name servers, and intermediary hosts are running. Your options depend on your implementation. Sends a certain number of packets and then stops. Specifies the number of milliseconds to wait before the lost message is lost or timed out. Sending pings with a longer timeout to identify latency issues. The pattern is a sequence of hexadecimal digits that fill the end of the packet. Use this if you expect routing problems and cannot find a route to the target node. Sends packages as soon as possible. Sends out prepackaged packages ASAP and returns to normal mode work. Good for finding out how many packets your router can handle in a short amount of time. Use this function to display a complete list of parameters and syntax. Manual setting network software should always be the last alternative.
- from the context menu select condition;
- in the opened window condition open the tab In detail;
- in a collumn Property find IPv4-server address;
- in a collumn Value
b) Windows XP:
- connect to the Internet;
- click the network status icon ("monitors" in the notification area Taskbars, next to the clock);
What does ping depend on?
When the kernel discovers a network card and creates a network interface, it assigns a name to the device. It depends on the order in which the device is recognized or the order in which kernel modules are loaded. Kernel default device names can only be predicted in very simple or highly controlled hardware environments. On systems where you can add or remove hardware at runtime, or enable automatic device configuration, no stable network devices are expected from the kernel beyond multiple reboots.
- in the opened window condition open the tab Intelligence;
- in a collumn Property find server;
- in a collumn Value find the address (for example, 100.100.100.100).
To create a shortcut to ping the provider's server (step-by-step process for Windows XP, for Windows Vista the differences are insignificant):
However, the system configuration tools require constant interface names. The program assigns permanent names to these interfaces instead of the names assigned by the kernel and stores them in the database. The line of this file describes the network interface and indicates its constant name. This section provides an overview of network configuration files explaining their purpose and format.
What is ping and what is it for?
These files contain configuration data for network interfaces. The following entries are included in the routing configuration file. The route is in the first column. The second column contains the default gateway or gateway to access the host or network. The third column contains the netmask for networks or hosts behind the gateway. Mask 255 is applied, for example, to a node behind a gateway.
- right-click on an icon-free surface Desktop;
- from the context menu that opens, select Create -\u003e Shortcut;
- in the opened window Create shortcut click the button Overview…;
- in the opened window Browse folders open up Computer -\u003e DiskC \\: (or D \\: if the operating system is installed on the D \\ :) -\u003e Windows -\u003e system32 -\u003e ping.exe -\u003e OK (after these manipulations in the text box Specify object placement the address will appear C: \\ WINDOWS \\ system32 \\ ping.exe) -\u003e Next;
Additional ping aggregates
The fourth column only applies to networks that are connected to the local host. This column should contain the device name. In the fifth column, you can indicate the type of route. Unused columns must contain a minus sign to ensure that the parser interprets the command correctly.
This file specifies the domain to which the host belongs. The status of the name server being accessed is also indicated. You can specify multiple domain names. When resolving a name that is not fully qualified, an attempt is made to create it by adding separate search records. If you are using multiple nameservers, enter multiple lines, each line starts with a nameserver. # Characters in front.
- in the next window you need to enter the name of the shortcut (by default it is offered ping.exe, but you can change this name to something else) -\u003e Done;
- on Desktop a newly created shortcut appeared ping.exe;
- right-click it, from the context menu that opens, select Properties;
- in the opened window Properties: ping.exe in the tab Label click in the text box An object after C: \\ WINDOWS \\ system32 \\ ping.exe, make one space and type the server that was found earlier (for example, 100.100.100.100), click OK.
They can be restored in a clean way, even if the reversal is done in a different order than the changes. In both cases, the changes are permanent. Changes made by the above services are only temporary. Each parameter must be on its own line. Comments are initiated with a # sign. # We named hosting hosts.
This is important for the performance of directory services. This is the computer name, so only the hostname without the domain name. This file is read by different scripts when the computer boots. It can only contain one line containing the hostname. You can test them before storing the configuration in config files.
Now, when you notice that your internet connection speed is dropping, try pinging the provider's server by clicking on the created shortcut.
Notes
1. Answers of the pinged server "Timed out request" or "The specified node is not available"usually indicate a problem with the ISP's server.
If you do not enter the configuration in the correct configuration files, the changed network configuration will be lost after restart. You can work with the following objects. This object represents network device... This object represents a routing table entry.
This object represents a multicast address. This object is a multicast routing cache entry. If no command is specified, the default command is used. After activating the device, you can configure it. For the connection to work, you must also configure the default gateway.
2. The firewall of the provider's server can be configured to block requests and responses, while normal operation of all network services is observed. In this case, there is no point in pinging it.
3. You can ping any network node, both local and The global... For example, you can ping a site to find it out, for this you need to use the utility ping with key -a (prefix http: // do not need to be inserted into the command).
An immediate response is required. If this happens, you will receive a message confirming that network connection working. The penultimate line contains information about the number of transmitted packets, lost packets and the total ping time. The default interval between two packets is one second.
Configure routing by route
Use a route to set up routing. In addition to the described configuration files, there are also several scripts that launch network programs when the computer boots. They run as soon as the system enters one of the multilevel runlevels. Some of the scripts are described in Table 9, “Some Startup Scripts for Network Tools”.
This is how a PC with Windows Vista ping the site google.ru, at the same time figuring it out:
C: \\ Users \\ Master\u003e ping -a google.ru
Exchange of packets with google.ru with 32 bytes of data:
Reply from 216.239.59.104: bytes \u003d 32 time \u003d 673ms TTL \u003d 236
Reply from 216.239.59.104: bytes \u003d 32 time \u003d 694ms TTL \u003d 236
Reply from 216.239.59.104: bytes \u003d 32 time \u003d 693ms TTL \u003d 236
Some startup scripts for network utilities. The network has many components. If they play together, it's okay. But woe, it doesn't work. Then a thoughtful and lengthy search begins. network error... This contribution leads the system to the search and helps to find the most common sources of errors. If you have a little time, you can get very far without network testing equipment and in-depth knowledge.
Network errors are widespread. Usually the cable is loose or not properly inserted. Often, however, unusual reasons are also the cause of evil: when mice are led to chess on a cable below the floor, cables are quickly made. All this has already happened and will happen hundreds of times. Here's our list to help you fix network errors.
Reply from 216.239.59.104: bytes \u003d 32 time \u003d 690ms TTL \u003d 236
Ping statistics for 216.239.59.104:
Packets: Sent \u003d 4, Received \u003d 4, Lost \u003d 0
(0% loss)
Valery Sidorov
In other words, how to check the availability of a router or server on the network. For this purpose, a simple ping utility utility is used, which is part of many operating systems... The program makes it possible to analyze the quality and availability of any network connection, whether it is a connection with remote server or home router.
The first ping is a nearby computer, server or Internet gateway. Based feedback with the server, so at least as soon as the connection is ok: However - this is only a connection to the addressed computer. Anyone who stops pinging is now weighing themselves in deceptive security. In any case, check the connections to the nameserver on your own network, the connection to the gateway and the file server... Because all connections to other computers on the network bring nothing, for example, if the gateway doesn't speak.
Only when all pings are successful can you assume that everything is physically correct. On the other hand, it is always easier if the equipment is in order. But where is the problem? Subsequently, allow this computer to resolve the local address, for example with.
ping is a service computer programdesigned to test connections in TCP / IP-based networks. It sends ICMP Echo-Request to the specified host and records the incoming responses (ICMP Echo-Reply). The time between sending a request and receiving a response (RTT, from the English Round Trip Time) allows you to determine two-way delays (RTT) along the route and the frequency of packet loss, that is, to indirectly determine the congestion of data transmission channels and intermediate devices.
If there is no correct feedback, you have probably found the culprit. If the computer is taken out of service, it does not automatically disappear in the host file. Or worse, the computer gets a different name on the network and is no longer accessible through hosts. This is a problem, especially in heterogeneous networks.
If there is no ping, check all lines. The simplest mistake is also the most common: network cable not connected. First check if all wires are connected. Then proceed as follows. If so, it indicates a working connection — at least the next switch or hub. Make sure that network Card firmly inserted into the socket. Problems may arise immediately after transporting the computer or performing maintenance work. Explore all existing wall outlets. Is the plug installed? Examine the connections on the patch panel. There should also be stubs here.
- Examine the network cable connected to the computer.
- Does it sit firmly and also does the plug sit?
- If the cover is loose, there may also be a loose contact.
- Check if the green LEDs on the back of the network card are flashing.
ping hostname or ping IP address
For example: to verify that the TCP / IP protocol is configured correctly on the local computer.
Ping 127.0.0.1
"loopback" - the computer makes an attempt to refer to itself. This check makes it possible to determine whether the computer can transmit Ethernet traffic or not. No response after running this command indicates a problem with the TCP / IP settings on the local computer.
Checking the availability of google.com
Ping google.com
Same:
Ping 74.125.143.113
The number of packages and their size can be adjusted using the parameters:
"-n number" - Specifies the number of packets to send. The default is 4.
"-l size" - The size of the ping packet. The default size is 32 bytes
Ping ya.ru -n 5 -l 100
5 packets of 100 bytes were sent.

By default, the ping command waits 4000 milliseconds (4 seconds) for every response, and if it fails, it displays the message "Request timed out". Then you can specify a longer timeout using the -w option. A "Request timed out" or "Specified host not available" response usually indicates a server problem.
"-w interval" - Interval specifies the amount of time to wait in milliseconds. The default is 1000 (the timeout period is 1 second).
Ping 192.168.0.1 -n 3 -l 50 -w 20000
to allow replies within 20 seconds, set ping-w to 20000

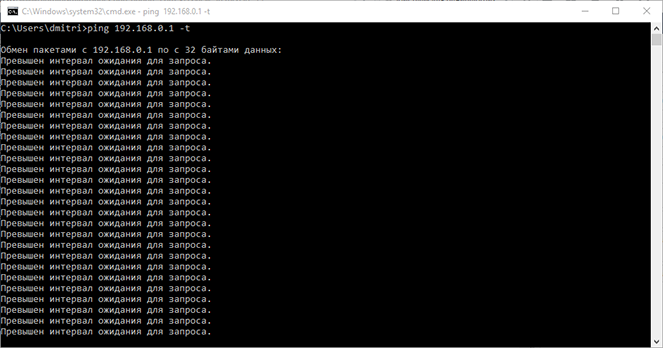
Ping 192.168.0.1 -t
"-t" The parameter means that packets will be sent in an infinite loop.
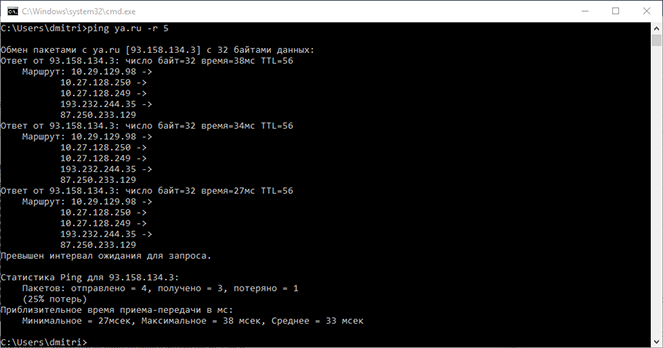
Ping ya.ru -r 5
"-r" The parameter is a counter. Records the route of packets sent and returned in the Record Route field. The counter parameter specifies the number of computers in the range from 1 to 9.
Other parameters:
A
Resolves computer name to address.
F
Sends packets with the Do not Fragment flag.
Packets will not break when passing through gateways on their route.
I ttl
Sets the TTL (Time To Live) packet time-to-live field.
V type
Sets the Type Of Service field of packets.
S number
Specifies the number of retransmissions on the route where the time stamp will be made.
J comp_list
Computers in the list can be separated by intermediate gateways
(free routing). Maximum number allowed by the protocol
IP is 9.
K comp_list
Directs packets along the route specified by comp_list.
Computers on the list cannot be shared by intermediate gateways
(limited routing). The maximum number allowed
iP protocol is 9.
