South Ural State University
Miass Engineering Faculty
Department of Quality Management and Standardization
Course work
In informatics
On the topic "Mail Server"
Introduction _____________________________________________________________3
Mail server _____________________________________________________________4
Email ____________________________________________________________5
Email address structure ____________________________________________6
What is a domain ______________________________________________________________7
History of the @______________________________________________________________ 9
Email software _______________________________________________________11
Mail.ru ______________________________________________________________________ 12
Yahoo! Mail _________________________________________________________________15
Rambler.ru __________________________________________________________________17
Leading email clients ___________________________________________________17
Conclusion _________________________________________________________________18
References ___________________________________________________________ 19
Introduction
Even in ancient times, people felt the need for information exchange and organized it at the state level. Therefore, the post office is one of the most well-organized institutions in the world.
Electronic mail is a new modern means of communication. Unlike regular mail, e-mail is transmitted electronic copies messages, files, programs, various data - i.e. information processed using a computer.
The main objects that make up the e-mail system are special computers called mail servers.
Mail server
Mail servers are servers that receive and send email messages.
The server receiving e-mails uses the Post Office Protocol (POP).
The server sending e-mails uses the Simple Mail Transfer Protocol (SMTP).
Mail server, email server, mail server - in the e-mail forwarding system, this is usually called the message forwarding agent (eng. mail transfer agent, MTA). it computer programwhich transfers messages from one computer to another. Typically, the mail server works behind the scenes, and users deal with another program - an email client. mail user agent, MUA).
Interaction scheme
For example, in a common configuration, the user agent is Outlook Express... When the user has typed a message and sent it to the recipient, the mail client communicates with the mail server using the SMTP protocol. The sender's mail server interacts with the recipient's mail server (directly or through an intermediate server - relay). On the recipient's mail server, the message enters the mailbox, from where it is delivered to the recipient's client using a mail delivery agent (MDA). Often, the last two agents are combined in one program, although there are specialized MDAs, which, among other things, are engaged in spam filtering. For the final delivery of received messages, not SMTP is used, but another protocol - often POP3 or IMAP - which is also supported by most mail servers. Although in the simplest MTA implementation, it is enough to put the received messages in the user's personal directory in file system central server ("mailbox").
Electronic mail (e-mail, from the Latin "electronic mail").
E-mail, like ordinary mail, works with a system of electronic "post offices" - mail servers, which ensure the forwarding of letters over global networks. They interact with the help of postal protocols that ensure the transfer and recognition of information transmitted in the network. Mail server client computers serve e-mail users. Everyone gets their own postal address and their own "mailbox" on this computer, i.e. memory area, as well as a password to access it.
Using a mail program, you can create messages, read them from mail server, work with the address book, store and organize letters in the folders of the "mailbox", prepare files for forwarding and convert them to desired format after receiving, etc.
Using the mail program, the user creates a message to the addressee, sets the address, sends the message, for which he connects to the mail server. During the connection, the mail server asks for a username and password. Otherwise, the communication session will not take place. After connection, the prepared mail is automatically sent to the server and then through transmission from one mail server to another reaches the addressee. Immediately after sending mail, the client automatically receives mail. Messages and files read into its memory area are sorted and put into user mailboxes. The addressee, when loading his mailbox, sees messages sorted into folders: new, old, sent. He can delete, sort and classify them as he sees fit.
Email address structure
When sending information, addressing is of great importance, since without it the recipient cannot be found. Everyone knows the sad story of Vanka Zhukov, who sent a letter to "grandfather in the village." Regular mail addresses are drawn up according to certain postal rules.
Existing design rules email addresses others. Email addresses have a clearer logical structure. They consist of a hierarchical sequence of domains - parts, for example:
All addresses consist of two parts, separated by the @ symbol (read "et"). When read from left to right, up to this character, the names of the users (recipients) are displayed. This can be the name of the postmaster - “post master”, fictitious or real names of the email users to whom the correspondence comes. Many of them can be registered on the same computer. The portion of the address to the right of @ identifies the computer connected to the network, city and country, or the name of the network in which the user is registered. Addresses are divided into parts called domains.
What is a domain
Considering a domain from right to left and dividing it into separate words, we get subdomains that specify in turn where to look for this mailbox. In analogy with regular mail, a domain is an address (the line "Where" on an envelope), and subdomains are the name of a country, city, street, house number.
The domain does not describe the path along which the message should be transmitted, but only explains where the addressee is; Likewise, the address on a postal envelope is not a description of the road the postman must take to deliver the letter, but the place where he must eventually bring it. In both cases, the postal services themselves choose the route to save time and money. Usually there are several ways in which a message can be delivered to a specified location, and when you send a letter, you do not know which of the ways it will go this time.
The rightmost subdomain (in our case, ru) is called the top-level domain and most often denotes the country code in which the server is located. The ru code is Russia, kz is Kazakhstan. Each code consists of two Latin letters. For example, the uk code stands for Great Britain, and the mailbox with the address [email protected] to be found in the English JANET network.
Each user working with mail applications, one way or another, is faced with setting the parameters of incoming and outgoing mail. One of the main elements is the configuration of the SMTP server. Consider what it is and how to make desired settings for different situations.
What is SMTP?
The abbreviation SMTP comes from the English phrase which means "simple mail sending protocol". Basically, its scope is limited to TCP / IP-based networks and the user layer.
In any mail program, often called, there are special settings that allow you to configure the parameters of the protocol. It is through him that everything emails sent to the mail server, where relaying is expected. Initially, the SMTP server uses TCP port 25. However, as e-mail services evolve, the settings can change significantly.
Do I need to configure the server when sending a letter from a mail service?
As a rule, anyone on the Internet offering services for sending and receiving e-mail to users is already equipped with a pre-configured SMTP server. That is, the user does not need to produce anything.
The services themselves, to enter their own mailbox, require the user only to enter the login and password specified during registration, and setting up, for example, the Mail.Ru SMTP server is not required just for the reason that in the service itself, all this was done initially (without this, the service would simply not work). But what to do if the user does not use Internet resources for some reason, but prefers standard clients like Microsoft Outlook Express and Outlook or third-party software products, while having a registered mailbox in the Internet service?
We configure the SMTP server (Mail.Ru is the mail service where the mailbox is registered)
Let's look at standard parametersto be applied to this service... Regardless of the used mail client absolutely all settings will be identical.
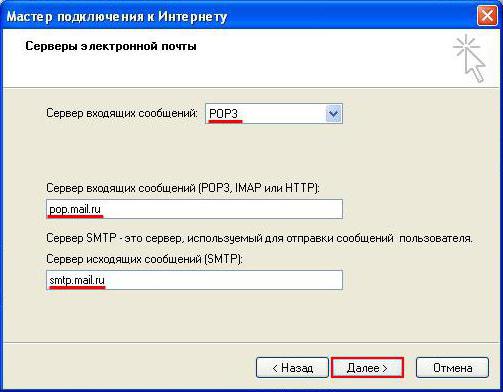
So, in order to properly configure the Mail.Ru SMTP server, you should set the following parameters:
- outgoing mail server - smtp.mail.ru;
- username - full name of the email address registered in the service;
- password - the current code combination of letters, numbers and symbols used to enter the box;
- port when SSL / TLS encryption protocol is selected - 465.
After these settings take effect, mail can be received directly in the user program you are using. As you can see, the port of the SMTP server differs from the standard one (25), but this is due to the TCP / IP protocols.
Configuring the SMTP server on Yandex
The Yandex.Ru service is no less popular. The SMTP server for it is configured in a completely similar way.
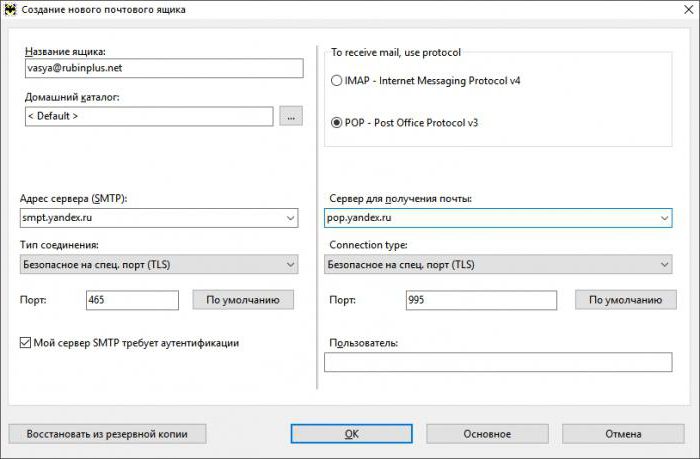
However, the smtp.yandex.ru address is used for the outgoing server, the port is set to 465, but only TLS is set in the security settings.
Installing an SMTP server for mailing
Now let's move on to more complex situations when the user for some reason (for example, to promote his own business or website) needs to send bulk. There is no point in doing this manually using online services or email clients, if only for the reason that it takes too much time and effort. Therefore, you can do it in two ways - buy a ready-made configured SMTP server or configure it yourself.
In the first case, if a "white" server is purchased, this will require significant costs, as well as compliance with all conditions of the developer or seller. You can, of course, purchase a "gray" server, but there is no guarantee that it will not be included in the spam databases of search engines. This is fraught only with the fact that the same Yandex, upon receipt of letters from the specified sources, will simply filter them and send them to the spam section, while Mail.Ru and Google mark the correspondence with the corresponding spam index. Setting up an SMTP server manually looks both more reliable and more economical in terms of financial costs.
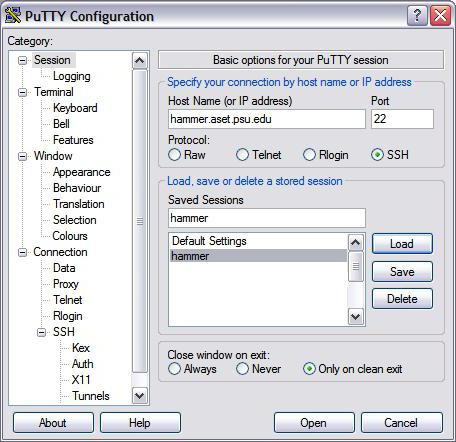
First you need to purchase a VPS server with the Centos operating system version no lower than the sixth. Notice immediately if it is possible to enter a PTR record that will accurately identify the canonical domain name by the receiving server.
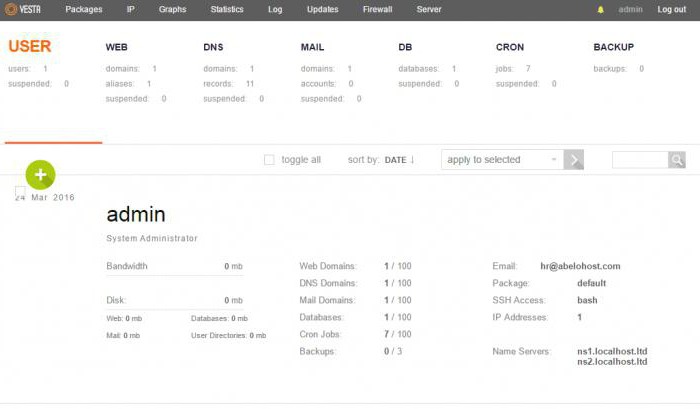
Next, you need to install the Vesta panel. As an example, we will use the PuTTY utility, which must be downloaded, installed and run. In the settings, immediately register the IP address of the server, then press the Open button and register the root login and password provided when purchasing a VPS server.
Now we sequentially enter the following commands:
curl -O http://vestacp.com/pub/vst-install.sh
bash vst-install.sh
If an error occurs, we solve it using the combination:
bash vst-install-rhel.sh —force
After that, enter a valid email address and hostname. The panel will be installed in 5-10 minutes.
https: // Server IP: 8083
A window appears where you need to enter root and the provided password.
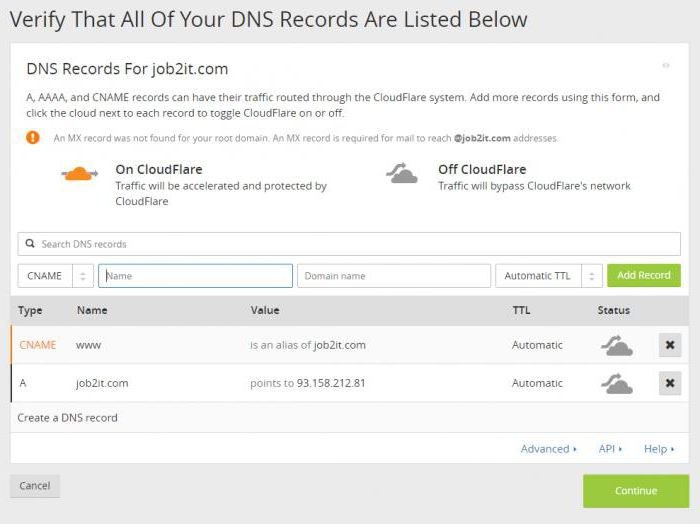
At the next stage, we register the domain and go to the DNS settings panel, where we swap the MX and A records.
We are waiting for the DNS zones to be updated, and go to the WEB tab in the Vesta panel, where we add the registered domain.
After that, we register SMTP accounts in the Mail section. To check in the same section, use the Open Webmail tab. In the opened window of the EXIM server, enter the parameters of the created SMTP and send a test letter. If everything is okay, you can congratulate yourself.
Please note that in some cases, bulk mailing may require digital signature (not to be confused with the PTR record, which is only responsible for the authenticity of the domain or host). In the absence of it, some receiving services may treat the mailing with suspicion, and the incoming mail itself will be marked as questionable. So you need to take care of this in advance.
Instead of an afterword
It remains to add that setting up an SMTP server for mail clients is not as difficult as it might seem at first. But for mass mailings, you will have to sweat over the setting, as they say. And you can use not only the option that was presented above. Some developers already offer automated systems creating and configuring such servers for a very reasonable fee (or even free of charge).
Instructions
Find out the server name by referring to the accompanying Windows Mail documentation, your ISP, or your network administrator. Note: mail Windows no longer supports the HTTP: // protocol, which is used by email services such as Hotmail, Gmail, and Yahoo. And to find out if the use of POP3, IMAP4 and SMTP servers is applicable for your OS, refer to the official Microsoft website (www.microsoft.com).
To find out the server settings, log into your email account with Outlook Web App. Select in sequence: "Options" - "Show all options" - "Account" - "My account"-" Options for POP, IMAP and SMTP access "(they can be found in another account menu, on the" Protocol Settings "page). However, if the setting for these servers says "Not Available", contact your ISP or network administrator for clarification.
Use the IMAP4 protocol whenever possible, as it has more capabilities as a mail server. If you have problems defining your server settings, refer to the Login and Password section of the documentation or contact your account manager.
If Windows Mail still fails to connect, check the authentication settings. Select the "Accounts" tab in the "Tools" menu, and then - the "Internet Accounts" item. Find your account and click the Properties button. Go to the "Servers" tab and make sure that the checkbox next to the "Use secure password verification" line is not selected.
You can find out the name of the server through which the messages were sent to you and, if necessary, block the connection by visiting the website http://who.is.
For example, you got a computer. Acquaintances gave the old system unit or were donated by relatives, in principle, the background is not so important. The first thing to know in this case is whether the Windows operating system is installed. This is not such a difficult question.
You will need
- - computer.
Instructions
Turn on your computer and wait for it to boot up. If Windows has booted, and the Start button, desktop and shortcuts appear on the screen, then on the computer the Windows operating system is clearly present. You can see the version and bitness of the operating system in the computer properties. To do this, click on the shortcut "My Computer", then right key mouse and select "Properties".
If, when the computer boots up, the process stops at the Windows label or appears blue screen with an error, it means that the operating system is installed, but cannot boot due to system failures. Restore old system using the console or service utilities, or reinstall it immediately - it's up to you.
If after turning on the computer, an inscription appears on a black screen, and the download does not proceed further, you need to decrypt this message. The ntldr is missing inscription means that the computer does not find boot partition... First of all, turn off the computer and check if the hard drive is connected to the power supply and the motherboard, and whether it is detected in the BIOS motherboard... If the hard drive is detected without problems, but the system is not downloading , go to the next item.
Use utility utilities or an alternative shell to inspect the contents of the hard drive. If you don't find on it windows folders, then, obviously, operating windows systems on the hard drive no. If all the required folders are there, and everything is in order with the equipment, but the system does not care not loaded , reinstall it.
Restore the old operating system after a serious failure, it is rather a thankless task than a useful one. After the restore, even if it succeeds, Windows may not work for long, and along the way it will torment you with constant errors.
Related Videos
A modern person spends a lot of time on the Internet. Therefore, over time, everyone has an impressive number of accounts on a variety of portals and sites. Finding out which sites you are already registered on is quite simple.

Instructions
During their time on the Internet, everyone has a unique story. It consists of ads and messages posted under its own nickname and accounts on various sites and portals. It is better to get rid of superfluous and irrelevant information of this kind for elementary reasons. information security... Another case is when it becomes necessary to remember whether you already have an account on a specific site so as not to re-register.
To find out your accounts records, you can start by searching the Internet for your own nickname. Enter in the search engine the nickname that you most often use when registering. In the search results, you will see links to almost all sites where an account from such a user was active. In order not to lose this information in the future, you can add all found Internet addresses to a special folder on the bookmarks bar.
To find out or remember if you have an account on a specific site, use the password recovery option. Without entering the data in the "Login" section, click on the "Remind password" link. In the field that appears, enter the email address that you usually use for registrations. If you already have an account on this resource, you will see a system message stating that password recovery data has been sent to the specified mailbox. Check your email and follow the instructions in the email you received.
So that in the future there will be no problems with clarifying information about existing accounts, create a special file and enter data on all new registrations into it. In this case, it will be very easy for you to clarify the information by simply using the search for such a document.
Maintain a special document that records all your registrations on Internet sites.
Server hacks happen every day. Hackers know hundreds of loopholes through which one or another level of access to the server can be obtained. In some cases, vulnerabilities allow you to get to the confidential data of users, sometimes the hacker gets full control over the resource. How to protect yourself from hacker attacks?

Instructions
To protect your server from hacking, you need to know the basic methods of hacker attacks. By closing possible loopholes, you significantly increase the security of your resource. All of the following is not of interest to hackers (they all know this very well), but it can be useful to server owners.
How is the server attacked? First of all, the hacker tries to understand what software installed on it. To do this, he can open a site located on the server and enter an erroneous request. In response to such a request, an incorrectly configured server issues an error message and accompanies it with something like this: Apache / 2.2.14 (Unix) mod_ssl / 2.2.14 OpenSSL / 0.9.8e-fips-rhel5 mod_auth_passthrough / 2.1 mod_bwlimited / 1.4 FrontPage / 5.0 .2.2635 Server at www.name_ server.com Port 80.
For a hacker, the above information can be very helpful - he sees the version of the installed HTTP- server (Apache / 2.2.14) and versions of other programs and services. Now he can search for exploits (malicious codes) for vulnerabilities in the versions of these services. And if the system administrator hasn't closed the existing loopholes, the hacker will be able to gain access to the computer. A properly configured server should not give any detailed information about itself or may display intentionally distorted information.
One of the simplest ways to hack, often giving results, is to view the folders on the server. Very often, administrators forget to set the rights to view them, so a hacker, having determined the structure of the site using the appropriate utilities, easily opens folders that are not intended for viewing. If the administrator is a novice, a hacker can find a lot of useful information in such folders. For example, login and password administrator. The password is usually encrypted with the md5 algorithm, but there are many services on the network to decrypt. As a result, the hacker gains complete control over the site. Conclusion: set the rights to read files and open folders.
Very often, hackers break into databases using the found sql vulnerabilities. There are special utilities that greatly facilitate the "work" of a hacker. With their help, in a matter of minutes, the presence of a vulnerability is determined, then the name of the database is determined, tables and columns are calculated, after which the hacker receives full access to information stored in the database - for example, usernames and passwords, credit card details, etc.
![]()
In today's innovative world, everyone has access to the Internet. Personal Computer can be compared to a house, and as the addressee receives letters in the mailbox in the real world, so it is necessary to communicate with people in the virtual. Therefore, it is impossible to do without an electronic mailbox. We propose to consider the option Mail.ru mail - the most common and reliable service.
Mail.ru is a huge platform that has a ton of communication tools, a search engine, and more recently, a unique currency. Not surprisingly, millions of emails are viewed here every day.
To start working with mail, you must register. We go to the Mail.ru website and on the left in the blue window select the phrase "Registration in the mail".

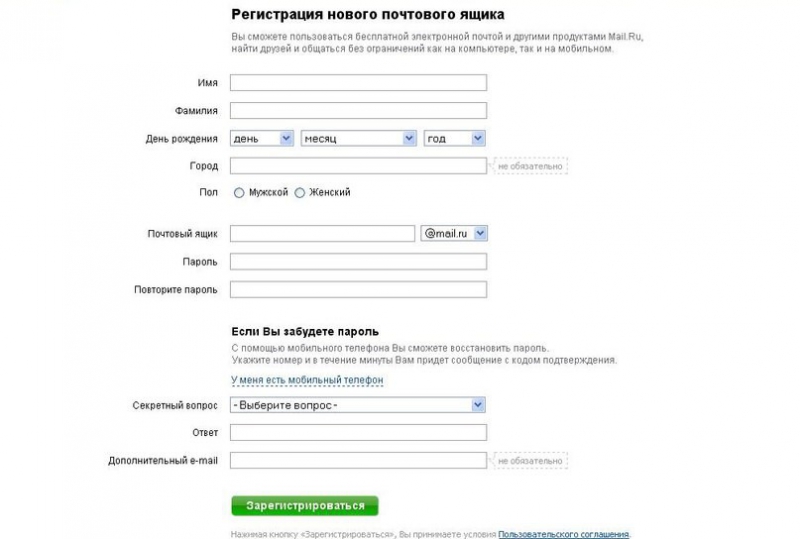
If everything is entered correctly, a unique login has been invented and you must click the "register" button. Do not ignore the paragraph “ Secret Question". The answer to it is necessary when recovering the password; it acts as an additional security measure.
Another required step is to verify your identity with mobile phone... To do this, you need to specify a valid number to which you will receive an SMS with a code. It must be entered into the specified window.
Together with by email the user will receive an account in My World and mail.ru Agent.
To enjoy by mailbox not necessarily only on the mail server. For ease of management, many different mail programs have been created. They are all different, but have identical settings. They will need the following information:
1. Configuring the incoming IMAP protocol
- server - imap.mail.ru;
- port 993;
- SSL / TLS protocol.
2.configuring POP3 protocol
- server - pop.mail.ru;
- port - 995;
- SSL / TLS protocol.
3.configuring outgoing SMTP
- server - smt.mail.ru;
- port 465;
- SSL / TLS protocol.
4.mailbox address and password
So, here we have specified the basic settings of the mail client on the mail.ru server. We hope that now using your mailbox will become even easier.
